Biden administration bans Kaspersky products in the U.S.
The United States Government has officially banned all Kaspersky products in the Country. Users will need to switch to alternative security products as the company can no longer sell its software in the U.S.
The Department of Commerce’s Bureau of Industry and Security published a document on its website, announcing the ban. It stated that Kaspersky has broad access and administrative privileges through its cybersecurity and antivirus software, which can grant them access to customer information. The announcement also mentions that Kaspersky employees could transfer sensitive information gathered in the U.S. to Russia, which could then be available for the Russian Government.
The Biden administration has accused Kaspersky of potentially using its products to install malicious software, or selectively deny updates, to leave American users and critical infrastructure vulnerable to malware. The ban also extends to third-parties that may integrate Kaspersky products in their software, so any antivirus that uses Kaspersky’s engine or software is also prohibited in the Country. The U.S. Govt has allowed software updates until September 29th, 2024. It is unclear whether users will get a refund from the security firm, or if they could update their antivirus manually to continue using the software beyond the said date.
Kaspersky has denied the allegations, stating that the Dept. of Commerce made its decision based on geopolitical climate and theoretical concerns instead of evaluating the integrity of its products. The Russian cybersecurity firm intends to pursue legal options to continue its business in the U.S.
Chrome will send your browsing history to Google if you use A.I. for search
Google is testing a new feature in Chrome that will give its A.I. access to user’s browsing history. This will allow users to use natural language to ask the A.I. to search through their history. The data is saved locally on the device in an encrypted form. However, Google says that Chrome will send the usage to its servers.
The data that is transferred includes “history search terms, page content of best matches, and generated model outputs”. This can be considered a privacy issue, and it gets worse. The Search giant has confirmed that the data may be accessed by human reviewers, in order to improve the feature. This suggests that the data may not be anonymized, so a user’s personal website or social profile could be revealed to Google. Users who are concerned about their privacy may disable the feature from the browser’s settings.
Qualcomm Snapdragon X Series laptops are reportedly not good for gaming
Reviews of new laptops powered by the Qualcomm Snapdragon X Series indicate that the devices offer great battery life. However, testers were left unimpressed by the gaming performance on the computers. The ARM-based chipset fared poorly in benchmarks across various games, and managed to deliver low frame rates even when upscaling technologies were enabled on 1080p low graphics settings in games like Baldur’s Gate 3, Cyberpunk 2077, to name a few.

Though the Snapdragon X series laptops ship with a powerful Neural Processing Unit, the NPU is not used for Copilot+ PC, as Microsoft’s A.I. tool relies on an online service to provide assistance to users.
YouTube wants users to allow tracking for personalized ads
YouTube has been tackling ad blockers quite aggressively for the past year or so. And now, the streaming service wants to track users further. The YouTube iOS app will soon ask users whether they want to allow it to track their activity on websites and other apps. The prompt will display two options: “Allow” and “Ask the app not to track”. If one chooses to grant permission to allow tracking, it will let the YouTube app monitor the user’s activity on websites and third-party apps to display personalized ads. This could compromise a user’s privacy. But, YouTube says that this will deliver a high-quality advertising experience. Users can change the option under the App’s Settings.
Microsoft adds 2 new features to its controversial Recall tool
Speaking of Microsoft’s A.I., the Redmond company is now testing two new features in Windows Recall. The tool came under criticism from users and security experts, who were alarmed at potential security and privacy risks that the automatic screenshot mechanism of Recall to expose user data to. The Redmond company reacted by postponing the roll-out of Recall, and actually had to remove it from the new Qualcomm Snapdragon X Series laptops, which caused delays for OEMs to ship the devices to reviewers.
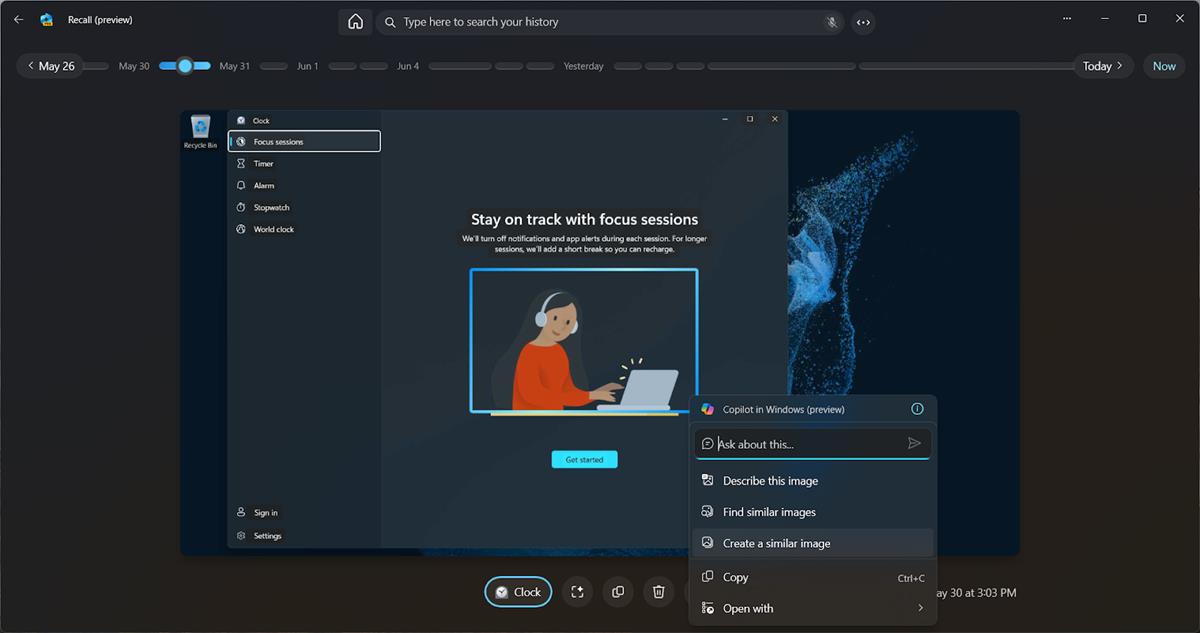
But, Microsoft seems to believe that Windows Recall can be useful for users. A recent Canary Build of Windows 11 introduces a feature called, Screenray, to Recall. This allows it to instantly analyses the content on the screen, which can then be used to interact with the A.I, you can ask questions about it. Unlike Recall, Screenray can be accessed independently with a keyboard shortcut.
The other feature, Topics, displays all snapshots captured in Recall, in a grid-view. Users can capture snapshots manually, assign tags to them, or let Recall add the tags. These tags act as categories to organize the data into collections. The collections are displayed in the home page of the app, and can be filtered using a search box.
Microsoft patches a Wi-Fi Takeover Attack vulnerability in Windows
Microsoft has revealed that it has patched a security issue in Windows operating systems that could have allowed hackers to take over a Wi-Fi network. The vulnerability has been tracked under CVE-2024-30078, and has been marked Important with a severity rating of 8.8/10 in the Common Vulnerability Scoring System.
Alarmingly, there are no special access conditions for this attack. A hacker just needs to be in the proximity of the Wi-Fi router to exploit the vulnerability, and breach the network. The hacker would not even need authentication to a victim’s PC.
The vulnerability could affect users who are connected to Wi-Fi networks at airports, coffee shops, hotels, trade shows, etc. Microsoft has patched the vulnerability in the June 2024 updates, so you should install the latest updates on Windows 10 and Windows 11 to protect your network and computers from the threat.